I was prompted to write this post as a result of Windows 10 Professional recently attempting to do a silent update while I was waiting in an airport which I unknowingly interrupted when I powered down my UEFI-based laptop prior to boarding the plane.
When I later powered on the laptop, it failed to boot and simply displayed the following message:
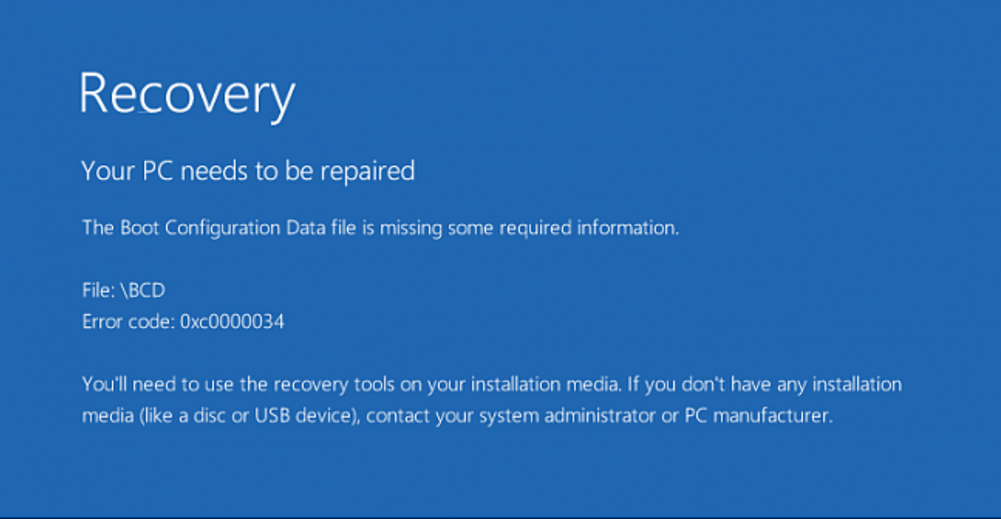
A Boot Configuration Data (BCD) store (there can be more than one) contains boot configuration parameters which control how the operating system is started in Windows 10. First introduced in Windows Vista, these parameters were previously stored in the boot.ini file on BIOS-based platforms and as NVRAM variables in UEFI-based platforms. If the BCD store is missing, becomes corrupted, or is not properly configured, Windows 10 will not boot.
Here are two graphics which provide an overview of how a UEFI-based platform boots into the Windows 10 operating system:
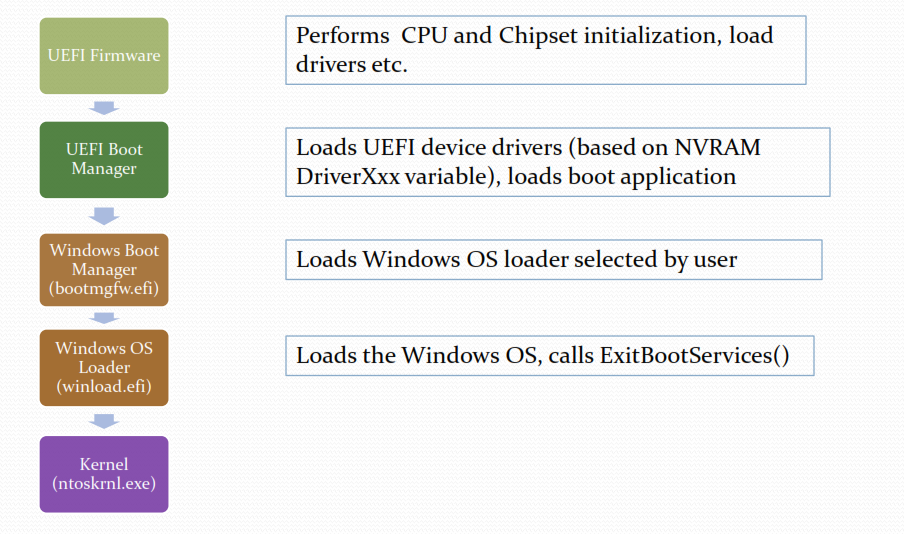
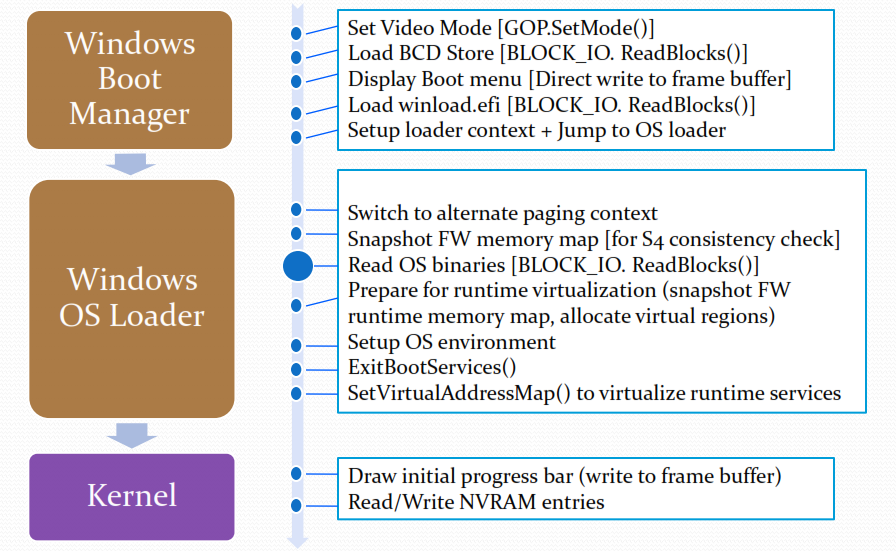
I assume by now that the majority of readers of my blog are quite familiar with UEFI-based platforms so the contents of the above graphics should be self-explanatory. Both graphics come from a UEFI-plugfest presentation by Murali Ravirala of the Microsoft Kernel Platform Architecture Team. Note that the Microsoft Boot Manager (bootmgfw.efi) is the only executable in the boot sequence which actually accesses the BCD store.
When you do an Internet search for how to fix BCD-related errors, you will find many articles explaining how to use the bootrec utility to effect the repair. Typically the described repair procedure is similar to the following:
X:>bootrec /scanos Scanning all disks for Windows installations. Please wait, since this may take a while... Successfully scanned Windows installations. Total identified Windows installations: 1 The operation completed successfully. X:>del d:\boot\bcd X:>bootrec /rebuildbcd Scanning all disks for Windows installations. Please wait, since this may take a while... Successfully scanned Windows installations. Total identified Windows installations: 1 [1] D:\Windows Add installation to boot list? Yes/No /All:
However, what is rarely pointed out to readers is the fact that the bootrec utility is not useful on UEFI-based platforms. It only works with with older BIOS-based systems which use an MBR (Master Boot Record) for booting!
On UEFI-based platforms, you should use the bcdedit command-line utility to manage BCD stores on your system. It has been available in all versions of Windows since Windows 7. Note that administrative privileges are required to use bcdedit to modify a BCD store. Furthermore, the BCD store is no longer located by default at c:>\boot\bcd but instead is located at /efi/microsoft/boot/bcd.
By the way, on a Windows 10 UEFI-platform you can delete the entire c:>\boot folder. It really serves no useful function except as a quasi-backup of the Windows-related boot files in the ESP. I deleted this folder and it’s contents when I installed Windows 10 and have never run into an issue with it not being there.
Here is what I saw on my laptop after I used my Windows 10 USB-based install media (never travel without a Windows 10 install media!) to get to a recovery command prompt and used bcdedit to enumerate all the default BCD store entries:
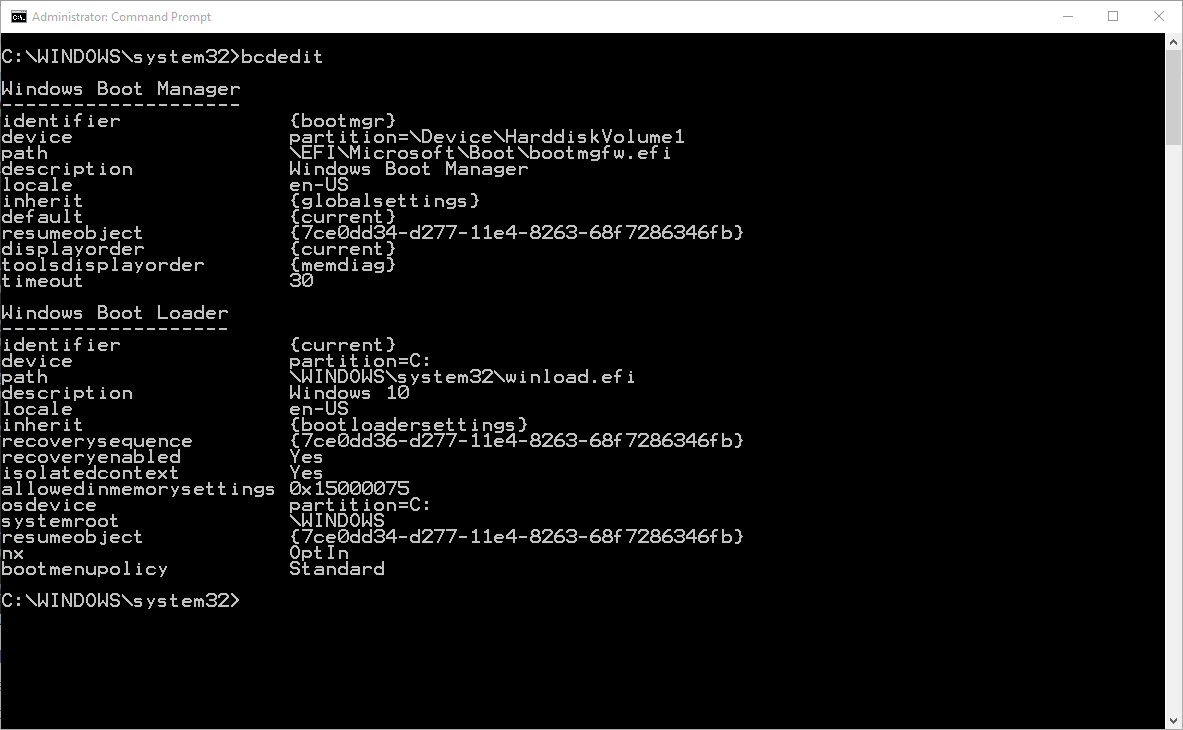
Both entries appear to be normal.
Note the extra (and critical for repairing the BCD store) information displayed when the /enum all switch is added:
C:\>bcdedit /enum all
Firmware Boot Manager
---------------------
identifier {fwbootmgr}
displayorder {bootmgr}
{def0c639-218c-11e6-845f-68f7286346fb}
{def0c63a-218c-11e6-845f-68f7286346fb}
{def0c632-218c-11e6-845f-68f7286346fb}
{def0c633-218c-11e6-845f-68f7286346fb}
{def0c63b-218c-11e6-845f-68f7286346fb}
{def0c63c-218c-11e6-845f-68f7286346fb}
{def0c63d-218c-11e6-845f-68f7286346fb}
{def0c63e-218c-11e6-845f-68f7286346fb}
{def0c638-218c-11e6-845f-68f7286346fb}
timeout 0
Windows Boot Manager
--------------------
identifier {bootmgr}
device partition=\Device\HarddiskVolume1
path \EFI\Microsoft\Boot\bootmgfw.efi
description Windows Boot Manager
locale en-US
inherit {globalsettings}
default {current}
resumeobject {7ce0dd34-d277-11e4-8263-68f7286346fb}
displayorder {current}
toolsdisplayorder {memdiag}
timeout 30
Firmware Application (101fffff)
-------------------------------
identifier {03426d41-d289-11e4-8264-806e6f6e6963}
description Diagnostic Splash Screen
Firmware Application (101fffff)
-------------------------------
identifier {03426d42-d289-11e4-8264-806e6f6e6963}
description Lenovo Diagnostics
Firmware Application (101fffff)
-------------------------------
identifier {03426d43-d289-11e4-8264-806e6f6e6963}
description Startup Interrupt Menu
Firmware Application (101fffff)
-------------------------------
identifier {03426d44-d289-11e4-8264-806e6f6e6963}
description Rescue and Recovery
Firmware Application (101fffff)
-------------------------------
identifier {03426d45-d289-11e4-8264-806e6f6e6963}
description MEBx Hot Key
Firmware Application (101fffff)
-------------------------------
identifier {def0c632-218c-11e6-845f-68f7286346fb}
device partition=\Device\HarddiskVolume1
path \EFI\fpm\SHELLX64.EFI
description UEFI 2.3 Shell
Firmware Application (101fffff)
-------------------------------
identifier {def0c633-218c-11e6-845f-68f7286346fb}
device partition=\Device\HarddiskVolume1
path \EFI\Boot\LenovoBT.EFI
description Lenovo BT
Firmware Application (101fffff)
-------------------------------
identifier {def0c634-218c-11e6-845f-68f7286346fb}
description IDER BOOT CDROM
Firmware Application (101fffff)
-------------------------------
identifier {def0c635-218c-11e6-845f-68f7286346fb}
description IDER BOOT Floppy
Firmware Application (101fffff)
-------------------------------
identifier {def0c636-218c-11e6-845f-68f7286346fb}
description ATA HDD
Firmware Application (101fffff)
-------------------------------
identifier {def0c637-218c-11e6-845f-68f7286346fb}
description ATAPI CD
Firmware Application (101fffff)
-------------------------------
identifier {def0c638-218c-11e6-845f-68f7286346fb}
description PCI LAN
Firmware Application (101fffff)
-------------------------------
identifier {def0c639-218c-11e6-845f-68f7286346fb}
description USB CD
Firmware Application (101fffff)
-------------------------------
identifier {def0c63a-218c-11e6-845f-68f7286346fb}
description USB FDD
Firmware Application (101fffff)
-------------------------------
identifier {def0c63b-218c-11e6-845f-68f7286346fb}
description ATA HDD0
Firmware Application (101fffff)
-------------------------------
identifier {def0c63c-218c-11e6-845f-68f7286346fb}
description ATA HDD1
Firmware Application (101fffff)
-------------------------------
identifier {def0c63d-218c-11e6-845f-68f7286346fb}
description ATA HDD2
Firmware Application (101fffff)
-------------------------------
identifier {def0c63e-218c-11e6-845f-68f7286346fb}
description USB HDD
Firmware Application (101fffff)
-------------------------------
identifier {def0c63f-218c-11e6-845f-68f7286346fb}
description Setup
Firmware Application (101fffff)
-------------------------------
identifier {def0c640-218c-11e6-845f-68f7286346fb}
description Boot Menu
Firmware Application (101fffff)
-------------------------------
identifier {def0c641-218c-11e6-845f-68f7286346fb}
description Diagnostic Splash Screen
Firmware Application (101fffff)
-------------------------------
identifier {def0c642-218c-11e6-845f-68f7286346fb}
description Lenovo Diagnostics
Firmware Application (101fffff)
-------------------------------
identifier {def0c643-218c-11e6-845f-68f7286346fb}
description Startup Interrupt Menu
Firmware Application (101fffff)
-------------------------------
identifier {def0c644-218c-11e6-845f-68f7286346fb}
description Rescue and Recovery
Firmware Application (101fffff)
-------------------------------
identifier {def0c645-218c-11e6-845f-68f7286346fb}
description MEBx Hot Key
Firmware Application (101fffff)
-------------------------------
identifier {def0c646-218c-11e6-845f-68f7286346fb}
description Startup Interrupt Menu
Firmware Application (101fffff)
-------------------------------
identifier {def0c647-218c-11e6-845f-68f7286346fb}
description Rescue and Recovery
Firmware Application (101fffff)
-------------------------------
identifier {def0c648-218c-11e6-845f-68f7286346fb}
description MEBx Hot Key
Firmware Application (101fffff)
-------------------------------
identifier {def0c649-218c-11e6-845f-68f7286346fb}
description IDER BOOT CDROM
Firmware Application (101fffff)
-------------------------------
identifier {def0c64a-218c-11e6-845f-68f7286346fb}
description IDER BOOT Floppy
Firmware Application (101fffff)
-------------------------------
identifier {def0c64b-218c-11e6-845f-68f7286346fb}
description ATA HDD
Firmware Application (101fffff)
-------------------------------
identifier {def0c64c-218c-11e6-845f-68f7286346fb}
description ATAPI CD
Firmware Application (101fffff)
-------------------------------
identifier {def0c64d-218c-11e6-845f-68f7286346fb}
description PCI LAN
Windows Setup
-------------
identifier {7254a080-1510-4e85-ac0f-e7fb3d444736}
device ramdisk=[C:]\$WINDOWS.~BT\Sources\SafeOS\winre.wim,{7ce0dd33-d277-11e4-8263-68f7286346fb}
path \windows\system32\winload.efi
description Windows Rollback
locale en-US
inherit {bootloadersettings}
osdevice ramdisk=[C:]\$WINDOWS.~BT\Sources\SafeOS\winre.wim,{7ce0dd33-d277-11e4-8263-68f7286346fb}
systemroot \windows
nx OptIn
bootmenupolicy Standard
winpe Yes
Windows Boot Loader
-------------------
identifier {current}
device partition=C:
path \WINDOWS\system32\winload.efi
description Windows 10
locale en-US
inherit {bootloadersettings}
recoverysequence {7ce0dd36-d277-11e4-8263-68f7286346fb}
recoveryenabled Yes
isolatedcontext Yes
allowedinmemorysettings 0x15000075
osdevice partition=C:
systemroot \WINDOWS
resumeobject {7ce0dd34-d277-11e4-8263-68f7286346fb}
nx OptIn
bootmenupolicy Standard
Windows Boot Loader
-------------------
identifier {7ce0dd36-d277-11e4-8263-68f7286346fb}
device ramdisk=[unknown]\Recovery\WindowsRE\Winre.wim,{7ce0dd37-d277-11e4-8263-68f7286346fb}
path \windows\system32\winload.efi
description Windows Recovery Environment
locale en-US
inherit {bootloadersettings}
displaymessage Recovery
displaymessageoverride Recovery
osdevice ramdisk=[unknown]\Recovery\WindowsRE\Winre.wim,{7ce0dd37-d277-11e4-8263-68f7286346fb}
systemroot \windows
nx OptIn
bootmenupolicy Standard
winpe Yes
Resume from Hibernate
---------------------
identifier {7ce0dd31-d277-11e4-8263-68f7286346fb}
device partition=C:
path \Windows\system32\winresume.efi
description Windows Resume Application
locale en-us
inherit {resumeloadersettings}
isolatedcontext Yes
allowedinmemorysettings 0x15000075
filedevice partition=C:
filepath \hiberfil.sys
bootmenupolicy Standard
debugoptionenabled No
Resume from Hibernate
---------------------
identifier {7ce0dd34-d277-11e4-8263-68f7286346fb}
device partition=C:
path \WINDOWS\system32\winresume.efi
description Windows Resume Application
locale en-US
inherit {resumeloadersettings}
recoverysequence {7ce0dd36-d277-11e4-8263-68f7286346fb}
recoveryenabled Yes
isolatedcontext Yes
allowedinmemorysettings 0x15000075
filedevice partition=C:
filepath \hiberfil.sys
bootmenupolicy Standard
debugoptionenabled No
Windows Memory Tester
---------------------
identifier {memdiag}
device unknown
path \EFI\Microsoft\Boot\memtest.efi
description Windows Memory Diagnostic
locale en-US
inherit {globalsettings}
badmemoryaccess Yes
EMS Settings
------------
identifier {emssettings}
bootems No
Debugger Settings
-----------------
identifier {dbgsettings}
debugtype Serial
debugport 1
baudrate 115200
RAM Defects
-----------
identifier {badmemory}
Global Settings
---------------
identifier {globalsettings}
inherit {dbgsettings}
{emssettings}
{badmemory}
Boot Loader Settings
--------------------
identifier {bootloadersettings}
inherit {globalsettings}
{hypervisorsettings}
Hypervisor Settings
-------------------
identifier {hypervisorsettings}
hypervisordebugtype Serial
hypervisordebugport 1
hypervisorbaudrate 115200
Resume Loader Settings
----------------------
identifier {resumeloadersettings}
inherit {globalsettings}
Device options
--------------
identifier {7ce0dd33-d277-11e4-8263-68f7286346fb}
description Windows Setup
ramdisksdidevice partition=C:
ramdisksdipath \$WINDOWS.~BT\Sources\SafeOS\boot.sdi
Device options
--------------
identifier {7ce0dd37-d277-11e4-8263-68f7286346fb}
description Windows Recovery
ramdisksdidevice unknown
ramdisksdipath \Recovery\WindowsRE\boot.sdi
Note the Windows Setup, Windows Recovery, duplicate Resume from Hibernate and more, and the two Windows Boot Loader entries. Duplicate entries are permitted but I personally like to have just one entry.
In general you will have the following entries in your default BCD store on a UEFI-based Windows 10 platforms:
- Windows Boot Manager
- Windows Boot Loader
- Windows Resume from Hibernate
- Windows Memory Tester
The Windows Boot Manager entry (Identifier bootmgr) manages the Windows 10 boot process. The entry specifies a boot manager called bootmgfw.efi, typically located in the ESP partition at \efi\microsoft\boot\bootmgfw.efi, loads a UEFI-based Windows loader which is located at c:>\windows\system32\winload.efi.
Microsoft publishes a number of documents on configuring the various BCD store settings using bcdedit. The best that I have come across is BCD System Store Settings for UEFI. Download and read this document in full before using bcdedit to modify the BCD system store!
Logically, a BCD store is a namespace container for BCD objects and elements that hold the information that is required to load Windows or run other boot applications. Using a BCD store provides a firmware-independent mechanism for manipulating boot environment data for any type of Windows system.
The BCD architecture is a hierarchy composed of three basic components:
- A BCD store is the top-level component in the hierarchy. It serves as the namespace container.
- A BCD object is a container of BCD elements. The most common type of BCD object describes a boot environment application, e.g. an instance of the Windows boot loader.
- A BCD element is a singular item of data such as a debugger setting, a boot application name, or an operating system device.

Physically, a BCD store is a binary file (hive) implemented using the standard Windows registry hive format. You can see the content of the BCD store used to boot Windows 10 using regedit or one of the many Windows registry viewers. Entries are stored under HKEY_LOCAL_MACHINE/BCD. The BCD that was used to boot windows is normally already mounted as BCD00000000.

Assuming you have administrator privileges, you can also view other BCD stores by clicking on HKEY_LOCAL_MACHINE, going to File->Load Hive and browsing to the BCD file you wish to mount, view, and edit entries.
According to Microsoft, a BCD store should not be accessed using registry APIs because of interaction with the underlying firmware. For this reason, BCD stores should be accessed only the available BCD tools or via the documented Windows Management Instrumentation (WMI) BCD provider. This WMI provider can be used to programmatically manipulate a local or remote BCD store.
By the way, it is possible to access the ESP from the command prompt if your have elevated privileges by assigning a temporary drive letter to the ESP using diskpart as shown below:

If you look at the contents of /efi/microsoft/boot, you will see two other files that form part of the Windows 10 boot process, i.e. bcd.log and boot.stl.
The BCD log files are the transaction journal(s) for the BCD store hive, and are for recovery purposes. They conform to the Windows registry file format specification.
As far as I know, there are no publicly available utilities to display the contents of such transaction logs in a useful format. Typically a hex editor such as WinHex is used.
Here, for example, is the first part of the base block for bcd.log:

Note the ASCII string regf. This string identifies a Windows registry format file. The DWORD at offset 4 contains the primary sequence number which is incremented by 1 in the beginning of a write operation on the primary file. The DWORD at offset 8 contains the secondary sequence number which is incremented by 1 at the end of a write operation on the primary file. The primary sequence number and the secondary sequence number should be equal after a successful write operation. The QWORD at offset 12 contains the last write timestamp. The ASCII string rmtm (Resource Manager, Transaction Manager) at offset 164 is a GUID signature first introduced in Windows 10.
The ASCII string HvLE at offset 512 indicates a log entry. Each log entry is stored at an offset divisible by 512 bytes and has a variable size which is a multiple of 512 bytes. There are no gaps between log entries. See the registry file format specification for more details.
Turning now to an examination of boot.stl which is another file found in the \efi\microsoft\boot folder. This file is a standard Microsoft certificate trust list (CRL).
d:>certutil -dump d:\efi\microsoft\boot\boot.stl
PKCS7 Message:
CMSG_SIGNED(2)
CMSG_SIGNED_DATA_PKCS_1_5_VERSION(1)
Content Type: 1.3.6.1.4.1.311.10.1 Certificate Trust List
PKCS7 Message Content:
================ Begin Nesting Level 1 ================
Certificate Trust List:
Version: 1
Usage Entries: 1
[0] 1.3.6.1.4.1.311.61.3.1 szOID_KMOD_REVOCATION_LIST
ThisUpdate: 9/30/2015 4:53 AM
NextUpdate: EMPTY
Subject Algorithm:
Algorithm ObjectId: 1.3.6.1.4.1.311.61.3.1 szOID_KMOD_REVOCATION_LIST
Algorithm Parameters:
05 00
CTL Entries: 0
Extensions: 3
1.3.6.1.4.1.311.61.3.3.1: Flags = 0, Length = 28
szOID_KMOD_CERT_MD5
0: 7e4d770dc4b5af90c7acf468f34d134e EMPTY
1: a1ecf42df0a819057b2b361c55ed2b13 EMPTY
1.3.6.1.4.1.311.61.3.3.2: Flags = 0, Length = 78
szOID_KMOD_CERT_SHA1
0: 0415f4e1565c3fef36cfd535c1346d7f... EMPTY
1: 08222b4d0f69d65f101e26605dd0b578... EMPTY
2: 0c873ebe4d199091c694ad3b1390f9c9... EMPTY
3: 226786f69cbbbfc959552d3688126d10... EMPTY
4: 2a0935479afbcf8455b932fc68a4a316... EMPTY
5: 795634617e813a70a87c05dd87b05bde... EMPTY
1.3.6.1.4.1.311.61.3.3.3: Flags = 0, Length = 3c
szOID_KMOD_CERT_SHA256
0: 1ee185a1a48b2ff301b641e91cdf3a98... EMPTY
1: 4ef556c930201cfaeee893102954a630... EMPTY
2: b68a22f66c3359c21ea9c523a1fa6728... EMPTY
---------------- End Nesting Level 1 ----------------
Signer Count: 1
Signing Certificate Index: 1
dwFlags = CA_VERIFY_FLAGS_CONSOLE_TRACE (0x20000000)
dwFlags = CA_VERIFY_FLAGS_DUMP_CHAIN (0x40000000)
ChainFlags = CERT_CHAIN_REVOCATION_CHECK_CHAIN_EXCLUDE_ROOT (0x40000000)
HCCE_LOCAL_MACHINE
CERT_CHAIN_POLICY_BASE
-------- CERT_CHAIN_CONTEXT --------
ChainContext.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
ChainContext.dwRevocationFreshnessTime: 3 Hours, 51 Minutes, 26 Seconds
SimpleChain.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
SimpleChain.dwRevocationFreshnessTime: 3 Hours, 51 Minutes, 26 Seconds
CertContext[0][0]: dwInfoStatus=122 dwErrorStatus=0
Issuer: CN=Microsoft Certificate List CA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
NotBefore: 8/19/2015 1:17 AM
NotAfter: 11/19/2016 1:17 AM
Subject: CN=Microsoft Revoked List Publisher, OU=AOC, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
Serial: 330000002112c797d2146f29c7000000000021
SubjectAltName: Directory Address:SERIALNUMBER="38138+1df1138b-b256-41f0-b413-8a5b1556a840", OU=AOC
Cert: d9e61ed62c65ca15366e0184aaeba245410d3f56
Element.dwInfoStatus = CERT_TRUST_HAS_KEY_MATCH_ISSUER (0x2)
Element.dwInfoStatus = CERT_TRUST_AUTO_UPDATE_END_REVOCATION (0x20)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
Application[0] = 1.3.6.1.4.1.311.10.3.19 Revoked List Signer
CertContext[0][1]: dwInfoStatus=112 dwErrorStatus=0
Issuer: CN=Microsoft Root Certificate Authority 2010, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
NotBefore: 3/30/2011 2:58 AM
NotAfter: 3/30/2026 3:08 AM
Subject: CN=Microsoft Certificate List CA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
Serial: 61116c92000000000007
Template: SubCA
Cert: b11264c19be7daa8c9e989176ae98961fade31cf
Element.dwInfoStatus = CERT_TRUST_HAS_KEY_MATCH_ISSUER (0x2)
Element.dwInfoStatus = CERT_TRUST_AUTO_UPDATE_CA_REVOCATION (0x10)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
Application[0] = 1.3.6.1.5.5.7.3.3 Code Signing
Application[1] = 1.3.6.1.4.1.311.10.3.1 Microsoft Trust List Signing
Application[2] = 1.3.6.1.4.1.311.10.3.9 Root List Signer
Application[3] = 1.3.6.1.4.1.311.10.3.19 Revoked List Signer
CertContext[0][2]: dwInfoStatus=13c dwErrorStatus=0
Issuer: CN=Microsoft Root Certificate Authority 2010, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
NotBefore: 6/24/2010 5:57 AM
NotAfter: 6/24/2035 6:04 AM
Subject: CN=Microsoft Root Certificate Authority 2010, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
Serial: 28cc3a25bfba44ac449a9b586b4339aa
Cert: 3b1efd3a66ea28b16697394703a72ca340a05bd5
Element.dwInfoStatus = CERT_TRUST_HAS_NAME_MATCH_ISSUER (0x4)
Element.dwInfoStatus = CERT_TRUST_IS_SELF_SIGNED (0x8)
Element.dwInfoStatus = CERT_TRUST_AUTO_UPDATE_CA_REVOCATION (0x10)
Element.dwInfoStatus = CERT_TRUST_AUTO_UPDATE_END_REVOCATION (0x20)
Element.dwInfoStatus = CERT_TRUST_HAS_PREFERRED_ISSUER (0x100)
Exclude leaf cert:
Chain: 66a8e7955fc5c41355ac9ae19f3b299de9ea9155
Full chain:
Chain: 7eb2aa2e9d03b7b78cba2e72eb9faf39fc1cdde9
------------------------------------
Verified Issuance Policies: None
Verified Application Policies:
1.3.6.1.4.1.311.10.3.19 Revoked List Signer
Signer Info[0]:
Signature matches Public Key
CMSG_SIGNER_INFO_PKCS_1_5_VERSION(1)
CERT_ID_ISSUER_SERIAL_NUMBER(1)
Serial Number: 330000002112c797d2146f29c7000000000021
Issuer: CN=Microsoft Certificate List CA 2011, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
Subject: CN=Microsoft Revoked List Publisher, OU=AOC, O=Microsoft Corporation, L=Redmond, S=Washington, C=US
Hash Algorithm:
Algorithm ObjectId: 2.16.840.1.101.3.4.2.1 sha256 (sha256NoSign)
Algorithm Parameters: NULL
Encrypted Hash Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA
Algorithm Parameters: NULL
Encrypted Hash:
0000 23 36 11 7d b2 aa bb ac 4a 51 8d 68 66 11 a6 93
0010 9f 50 40 bc b4 bc a8 b7 52 32 5b 5c 25 00 10 a4
0020 bd 2a 51 9a dd ea e5 62 c2 00 e5 30 6e 9d f8 cc
0030 24 e7 01 00 fd e7 4b 3e 96 7d 40 cf 5e 26 a7 c3
0040 57 0b f7 29 b3 a8 4c 8f b8 a7 2b 57 45 52 d2 bf
0050 66 2c 7e c9 44 46 49 2a 67 c6 84 b8 aa 81 6c 64
0060 a6 c2 69 2e 05 b9 ab d3 14 ba ca ef 29 20 57 c4
0070 d9 ee 65 b9 d4 2a 9d bc bf 4e b8 ff 3a 9b 5b 20
0080 33 e1 92 10 01 fb c8 dd 98 73 1d 89 70 96 b1 85
0090 a4 74 0f 00 12 08 03 73 28 39 74 09 27 a5 2d c8
00a0 e3 e4 92 f0 c2 be 51 c8 94 1a 6c 0b 4f c1 3e 1d
00b0 29 4a 97 8f 7f 91 44 df c6 4c 42 ce 57 ad ab 72
00c0 09 7e b3 83 21 d0 6f 5e 54 cd 36 15 e1 e9 7b 2e
00d0 8e 51 27 12 21 58 92 9e b2 0d e9 19 dd d1 28 44
00e0 f6 4b ec 3d 9a 3f 8a 13 6b 67 3d 09 92 56 f6 09
00f0 3a d5 56 05 34 65 89 de 45 56 8f 90 5c 50 80 7b
Authenticated Attributes[0]:
3 attributes:
Attribute[0]: 1.2.840.113549.1.9.3 (Content Type)
Value[0][0], Length = b
1.3.6.1.4.1.311.10.1 Certificate Trust List
Attribute[1]: 1.2.840.113549.1.9.4 (Message Digest)
Value[1][0], Length = 22
Message Digest:
0000 46 07 27 aa 07 30 2a 6f ac e0 35 e3 b9 14 13 5b
0010 85 40 16 58 aa d0 09 8d 3c 70 76 1e bf 8a ed 35
Attribute[2]: 1.3.6.1.4.1.311.2.1.12 (SPC_SP_OPUS_INFO_OBJID)
Value[2][0], Length = 4c
Description: Microsoft Corporation
Url: http://www.microsoft.com
Unauthenticated Attributes[0]:
0 attributes:
Computed Hash: ...
0000 9f 2a 9d e6 34 b6 fa b6 99 9e 6e 7b 07 67 0b bf
0010 89 96 b0 57 1e e4 24 66 ae 7c 86 68 c9 b1 8f bc
No Recipient
Computed Hash: ...
0000 9f 2a 9d e6 34 b6 fa b6 99 9e 6e 7b 07 67 0b bf
0010 89 96 b0 57 1e e4 24 66 ae 7c 86 68 c9 b1 8f bc
Certificates:
================ Begin Nesting Level 1 ================
Element 0:
X509 Certificate:
Version: 3
Serial Number: 61116c92000000000007
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
CN=Microsoft Root Certificate Authority 2010
O=Microsoft Corporation
L=Redmond
S=Washington
C=US
Name Hash(sha1): 36c61e7e4edbe33d203ae1c16d5e7d8a6f9d8f23
Name Hash(md5): 83d006c6d15405e6ce2847a90a3f3ec9
NotBefore: 3/30/2011 2:58 AM
NotAfter: 3/30/2026 3:08 AM
Subject:
CN=Microsoft Certificate List CA 2011
O=Microsoft Corporation
L=Redmond
S=Washington
C=US
Name Hash(sha1): ecca5efef031521a908d56622ab07e1f4b6cf95b
Name Hash(md5): 092ae8851478335ff5420029522550fa
Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA
Algorithm Parameters:
05 00
Public Key Length: 4096 bits
Public Key: UnusedBits = 0
0000 30 82 02 0a 02 82 02 01 00 b8 84 7a 80 fd 4d 27
0010 a7 d2 ef 82 36 f1 53 05 9d be 42 6d 8e 31 08 47
0020 cb cd b3 83 0a 4b 4e 33 1a 2e 7c dd 72 81 8d ce
0030 90 fc 3c 05 cb 2f 34 85 38 8f 3c 1c 68 6d 60 51
0040 52 4d ac da 6d 2b 7e b3 73 47 ab d2 dc 95 71 4a
0050 31 81 5a a1 1f ab 82 26 45 2d 8c e8 84 78 bd 20
0060 f0 0d c6 f5 ae 26 87 1e 56 8e 55 3c 08 30 32 94
0070 94 22 93 0b a5 b0 c6 5d e6 2d 81 39 cd e9 c7 ae
0080 e8 d8 49 71 49 ab 91 74 b8 4f 8d 2f 47 b3 3f d0
0090 93 83 5c 02 1a de 4b b8 b2 3c 37 e9 93 ea 72 5b
00a0 98 c7 e3 ac 18 e0 e6 7e 4a c1 81 2c fd 22 14 76
00b0 73 e1 68 dc 20 09 c0 f3 46 cd 23 26 c8 45 22 ca
00c0 c7 bc 74 fc 89 ff 57 e0 cf bd 8e b0 2b ef 26 d6
00d0 77 ab 1a f4 67 41 f1 5e 0c 71 aa 02 7f 5e c0 82
00e0 aa 09 8b ec 89 88 41 f5 03 42 69 d9 1f 45 d9 57
00f0 3e 04 96 4a d5 32 b7 d1 61 26 68 c7 c1 b1 a0 e0
0100 7a 05 4e b5 6d c2 82 e0 2e b6 e7 64 9f 16 7d 95
0110 2a 86 32 d0 21 c8 5d f8 cb 05 30 1e b9 02 98 6c
0120 b3 93 6b c8 83 67 21 5d d6 65 98 20 64 dd cb bf
0130 47 9b ff 18 fa f1 90 de a7 78 cd 7b 04 86 7e 27
0140 8a b7 95 9c 26 dd b1 96 fc 4f e0 40 20 83 68 dd
0150 ec 33 f2 2a a0 07 a7 eb 91 fa ac 0f 51 41 88 f1
0160 c5 87 41 4c 87 47 62 9d 58 c0 9e 7f bb 12 7d de
0170 d3 9f fd c1 c7 14 bd 7f 98 d0 57 9b e1 e3 6c 57
0180 e1 65 5f f0 dc 2b 9c a1 54 c2 56 2a 15 64 cb aa
0190 4e e4 fd c3 e8 77 88 ff db 0d af 90 9f d7 68 81
01a0 01 2f 94 e1 af c6 e4 c6 76 db 75 da df d0 12 4c
01b0 f2 89 36 6f 48 80 81 58 dd 17 09 28 2b 55 ac 93
01c0 23 e5 8e 31 65 ad 0d 8e 93 d3 71 a7 81 14 98 e9
01d0 ac aa 05 58 ee d7 44 43 30 6d 1d c7 ba c2 7f f5
01e0 48 c4 e5 a0 8e 55 8e b4 09 c0 01 c3 9d 1d 46 f5
01f0 fe 46 b5 3a 00 88 23 b5 f0 ca 41 cd 3b 0d c6 f6
0200 ca 40 04 ea 9b e5 88 36 9f 02 03 01 00 01
Certificate Extensions: 9
1.3.6.1.4.1.311.21.1: Flags = 0, Length = 3
CA Version
V0.0
2.5.29.14: Flags = 0, Length = 16
Subject Key Identifier
41 f0 21 c7 ed c4 87 fa 83 75 ff 0a 0c dc 2d ec a8 6a ab 59
1.3.6.1.4.1.311.20.2: Flags = 0, Length = c
Certificate Template Name (Certificate Type)
SubCA
2.5.29.15: Flags = 0, Length = 4
Key Usage
Digital Signature, Certificate Signing, Off-line CRL Signing, CRL Signing (86)
2.5.29.19: Flags = 1(Critical), Length = 5
Basic Constraints
Subject Type=CA
Path Length Constraint=None
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=d5 f6 56 cb 8f e8 a2 5c 62 68 d1 3d 94 90 5b d7 ce 9a 18 c4
2.5.29.31: Flags = 0, Length = 4f
CRL Distribution Points
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl
1.3.6.1.5.5.7.1.1: Flags = 0, Length = 4e
Authority Information Access
[1]Authority Info Access
Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2)
Alternative Name:
URL=http://www.microsoft.com/pki/certs/MicRooCerAut_2010-06-23.crt
2.5.29.37: Flags = 0, Length = 30
Enhanced Key Usage
Code Signing (1.3.6.1.5.5.7.3.3)
Microsoft Trust List Signing (1.3.6.1.4.1.311.10.3.1)
Root List Signer (1.3.6.1.4.1.311.10.3.9)
Revoked List Signer (1.3.6.1.4.1.311.10.3.19)
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 fb dc ed bd c9 64 b5 93 4f ae a8 76 10 12 d6 cc
0010 e7 5c da 1e 51 d3 11 d6 7d b1 90 71 8a 86 a2 85
0020 cf 8b e5 a4 62 1a 7a 4a 52 66 09 ee 07 07 e1 0e
0030 18 7c 4d f4 1a 7d 44 99 69 f7 2d ff c0 85 56 14
0040 50 8a 54 e0 b1 23 2a 61 85 47 0a d2 34 0d bc 26
0050 0a ed 1f fb 8a e3 0e 48 5a 54 57 67 0d b9 66 37
0060 6e 4b 82 43 9d d2 33 e5 8e d7 64 a9 db b9 0f 2e
0070 a6 5b 10 1e c7 42 e9 28 f6 56 0e b9 a6 90 60 93
0080 df f1 33 cb 19 25 eb e6 3e e9 92 97 d4 94 e0 5a
0090 bb 3f 2d e1 36 05 48 ad 12 0e ad 0f b1 03 df 0f
00a0 49 96 46 b7 cb 47 02 9c 16 44 0c 67 ac 0b e0 0f
00b0 60 99 b6 91 d9 35 db 1a 04 eb 36 1d f1 10 cd 53
00c0 92 dd 2e 41 10 eb ff 56 3a 94 cc c6 3d 51 4c 92
00d0 a2 fe d1 33 6b 5d 27 72 1b e9 d2 9b 1f 57 bf 59
00e0 83 db 0d 25 66 7e 39 7f 16 cd d1 b8 92 58 d3 89
00f0 3b d5 bd 98 e4 f9 7b ef a4 bb 6e 83 42 26 e5 27
0100 27 2e 74 1e 55 18 0d 4b d0 66 7f a6 44 36 1f b8
0110 e9 4f 75 f0 b8 05 76 a6 5b 1d 5c a9 5b e3 83 43
0120 4c f9 0b 30 ef 11 36 f9 31 bf 2e 78 33 f2 2a d8
0130 6b bf d4 54 ee 50 10 b3 e5 55 8b 36 77 bf fe 3f
0140 8b fd b7 4d a7 3a ea 56 31 25 3d 9c 9a 14 1f 48
0150 af 82 f9 2f 4a ae dd 29 03 ee 19 01 2d 37 5b 39
0160 49 74 6a b4 a3 6b 30 ad f9 3e f9 c1 8c 8d 1a 74
0170 79 30 44 dd 1a e7 6d 6d 04 04 29 23 5d 34 a6 ae
0180 cf 37 de 21 e1 d2 19 14 87 ef 94 12 55 0b 0b e9
0190 25 ef 32 c6 47 e3 6f 08 c4 af a9 bf d3 ab 09 5a
01a0 dc 3e d8 34 e5 c7 75 69 3b 96 82 1a b1 68 69 81
01b0 4c 37 00 1c 9b 13 40 d0 b6 7c 36 41 2b dc 10 51
01c0 2d 8d cc 20 8f db 16 74 36 40 3e 13 29 28 79 49
01d0 a5 e9 01 9d db 42 ea 50 0c 44 50 79 f6 fb ff f8
01e0 99 f2 ad be 43 5d 0f a8 c8 a8 a7 f9 7d 2b ab f0
01f0 41 9c 62 0f 34 27 41 59 c8 e5 bf b3 a5 a9 f7 82
Non-root Certificate
Key Id Hash(rfc-sha1): 41 f0 21 c7 ed c4 87 fa 83 75 ff 0a 0c dc 2d ec a8 6a ab 59
Key Id Hash(sha1): 8b 15 14 1f e2 d3 d2 3a 84 20 d4 2a 55 4a 79 df c3 f0 55 40
Key Id Hash(md5): 94ff0d17649573c35e06543c8ce19539
Key Id Hash(sha256): 4c4499a0c520ffff7d2f84fda3c40db4f70ee119d6a091745333070ef493037d
Cert Hash(md5): 09 14 90 7e 1f 61 10 43 e6 40 0f fb 7f d1 8d 41
Cert Hash(sha1): b1 12 64 c1 9b e7 da a8 c9 e9 89 17 6a e9 89 61 fa de 31 cf
Cert Hash(sha256): a53a400df29ec7b8c8fce7cfffe47334f43b1642e604dd0307491737ebbc00ce
Signature Hash: 7d4e39e7a6adcbfe591742255153d9808e3e59ef0cc8bac6196351be8464c286
---------------- End Nesting Level 1 ----------------
================ Begin Nesting Level 1 ================
Element 1:
X509 Certificate:
Version: 3
Serial Number: 330000002112c797d2146f29c7000000000021
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Issuer:
CN=Microsoft Certificate List CA 2011
O=Microsoft Corporation
L=Redmond
S=Washington
C=US
Name Hash(sha1): ecca5efef031521a908d56622ab07e1f4b6cf95b
Name Hash(md5): 092ae8851478335ff5420029522550fa
NotBefore: 8/19/2015 1:17 AM
NotAfter: 11/19/2016 1:17 AM
Subject:
CN=Microsoft Revoked List Publisher
OU=AOC
O=Microsoft Corporation
L=Redmond
S=Washington
C=US
Name Hash(sha1): 0df7ace1921119f33f205e5faefad800827eb034
Name Hash(md5): 02ee2457cc24be35af8aaf7ef42adb9b
Public Key Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.1 RSA (RSA_SIGN)
Algorithm Parameters:
05 00
Public Key Length: 2048 bits
Public Key: UnusedBits = 0
0000 30 82 01 0a 02 82 01 01 00 a3 06 c3 a3 90 77 e5
0010 44 b4 79 c8 c2 27 8d a2 d2 4d ef 1c 46 0b c9 9d
0020 e3 80 a1 c8 af fb 51 7a dc c5 f0 6a 89 8c 6f a9
0030 a5 d6 c6 f7 8e f9 b6 80 3f ad 86 d3 ff ee be 62
0040 91 c2 6d 76 79 dc 2e b1 5e dc dc 3f d8 cf 0f 8a
0050 00 02 39 b7 f0 77 58 4c 3c 17 25 e3 e4 3b 27 45
0060 39 e3 97 0e c5 65 17 83 52 72 23 c4 fd bb f9 d8
0070 76 d3 8e cd e4 92 5e 2f ea 0c a5 23 fe 02 5d 80
0080 91 fd 98 9b 6d c2 55 4b 4e 71 70 86 aa 74 25 f5
0090 be 8e e2 f2 2c b4 75 05 c7 09 04 bd 40 87 9c 51
00a0 f6 f9 d8 5f f8 e2 03 c0 7c 25 f0 69 41 90 09 25
00b0 1e 5c b9 63 01 10 0f cd 3c eb 14 28 4c b3 4c 82
00c0 2c 43 b8 8d bf 0b 70 a4 30 26 6a af 5c 4a 95 03
00d0 9d 74 f6 7d 94 2b 04 d0 a1 75 58 07 4a 9e 88 71
00e0 d4 cf a0 26 85 f1 f3 5b 5b 03 54 13 a9 2d f3 5e
00f0 b1 aa 7b 9c 88 35 4c 34 d5 8a c4 b4 3e 8c 4a 29
0100 9c 49 b6 1c fb 8d 1c 32 e9 02 03 01 00 01
Certificate Extensions: 7
2.5.29.37: Flags = 0, Length = e
Enhanced Key Usage
Revoked List Signer (1.3.6.1.4.1.311.10.3.19)
2.5.29.14: Flags = 0, Length = 16
Subject Key Identifier
a8 a0 0d ca 73 8e 73 04 a8 24 ed dd 56 5e 83 e8 0c 01 55 86
2.5.29.17: Flags = 0, Length = 49
Subject Alternative Name
Directory Address:
SERIALNUMBER="38138+1df1138b-b256-41f0-b413-8a5b1556a840"
OU=AOC
2.5.29.35: Flags = 0, Length = 18
Authority Key Identifier
KeyID=41 f0 21 c7 ed c4 87 fa 83 75 ff 0a 0c dc 2d ec a8 6a ab 59
2.5.29.31: Flags = 0, Length = 52
CRL Distribution Points
[1]CRL Distribution Point
Distribution Point Name:
Full Name:
URL=http://crl.microsoft.com/pki/crl/products/MicCerLisCA2011_2011-03-29.crl
1.3.6.1.5.5.7.1.1: Flags = 0, Length = 51
Authority Information Access
[1]Authority Info Access
Access Method=Certification Authority Issuer (1.3.6.1.5.5.7.48.2)
Alternative Name:
URL=http://www.microsoft.com/pki/certs/MicCerLisCA2011_2011-03-29.crt
2.5.29.19: Flags = 1(Critical), Length = 2
Basic Constraints
Subject Type=End Entity
Path Length Constraint=None
Signature Algorithm:
Algorithm ObjectId: 1.2.840.113549.1.1.11 sha256RSA
Algorithm Parameters:
05 00
Signature: UnusedBits=0
0000 66 6d 81 e8 24 ff 5a 70 14 a0 ed 81 76 e9 05 4f
0010 86 63 2f 91 42 0d e9 50 50 09 de 47 a6 1d a7 df
0020 16 fc 7f 6d 0e 72 47 09 18 cd 29 14 d8 5e 6b fd
0030 16 86 ea 2f 9f e6 d6 ac 57 94 f1 df 4e d1 e0 d0
0040 1e 8a 26 b8 54 aa d8 a5 0f 2e 16 d1 23 bf 8b ac
0050 ee f0 ea 02 06 da 58 7d 2b e9 0d d5 25 48 df d6
0060 a5 b7 25 49 29 5f a7 67 13 d5 c5 64 51 6e 9c ed
0070 1f 3b 7b 44 ec 46 17 27 a7 96 40 a8 d3 bf b4 46
0080 05 12 f8 d6 72 9f d2 cb 79 6a 1f a9 cf 1e 34 ee
0090 f7 3d 9a 02 d5 c9 64 8f c3 ab f4 57 b2 1d 50 e7
00a0 7f b2 52 c3 06 3e e7 fa a9 5f 23 8d a4 d1 01 30
00b0 21 8a 8a 34 6f c8 d8 ee 0a e6 c2 af cf dc 20 c3
00c0 e9 ae 86 4a dd 41 e0 73 37 ae bc d8 2e d4 87 70
00d0 3f 38 c4 05 11 0c b7 21 0a 3a fb 7e 11 b7 ea 8d
00e0 41 b3 74 4e 80 79 82 64 a6 83 e1 46 c3 48 cf d6
00f0 c1 e2 b7 56 93 2a 66 2b 09 cf 82 c6 6e d7 02 56
0100 f9 cc a8 44 27 b7 91 19 cc 1e 79 b8 2a e5 82 27
0110 49 bc 4d 89 f4 8f 5f 9d bb 00 86 94 8a e5 c3 f1
0120 e8 8c 01 e7 53 28 5b b5 ce 5d 6a 60 ae ed b7 03
0130 cd 09 fc 52 46 f4 61 3b e8 99 69 64 11 52 fd 1a
0140 c6 9b e0 63 99 60 50 8b cd c8 1e ec a6 ab 6f d9
0150 59 cf 96 20 bd 98 cc e2 12 9a 1e 8b b6 7d 2d ca
0160 42 7a 0c 34 3d cc 45 cd fe 71 b9 fb 5c cd ea a9
0170 0b 39 c3 bc b7 59 1c b4 fc 0a 17 8b 4c 81 17 5b
0180 be 4e 46 74 dd 59 76 48 6f 87 0d 9a 29 a5 85 07
0190 b0 5d 02 56 53 5b 93 4f 72 0f 9b ab 95 e8 7b 55
01a0 17 72 3b f6 5f c3 ab c0 01 1e 56 01 23 49 de 3d
01b0 d1 8b d3 af 21 a4 3f a5 a8 74 fd 3e 85 2d 0a d2
01c0 4d 07 f3 7f 55 70 b7 77 80 1b aa f7 6d b1 fe 0f
01d0 17 94 d1 34 c9 4d 9c 89 09 94 96 9f e8 4d f4 0a
01e0 94 c7 6a a3 dd cb e8 83 dc ab 61 b0 08 10 66 3a
01f0 18 b1 9b 37 3d 3f 9c 55 1e 7c 38 dc e0 8b 80 2b
Non-root Certificate
Key Id Hash(rfc-sha1): a8 a0 0d ca 73 8e 73 04 a8 24 ed dd 56 5e 83 e8 0c 01 55 86
Key Id Hash(sha1): bc 23 44 2a e5 27 32 3f 28 99 bf f6 1e 35 b9 86 88 f9 1a fb
Key Id Hash(md5): 8b66a98e0818960cfb6dcf5e8e48a3e4
Key Id Hash(sha256): d8934114a0abae329ac981f69be56b573b197900554a945f3c20f76565ff4f75
Cert Hash(md5): 72 e9 55 5a d5 d5 54 ba d2 02 6e f6 42 b2 8d d2
Cert Hash(sha1): d9 e6 1e d6 2c 65 ca 15 36 6e 01 84 aa eb a2 45 41 0d 3f 56
Cert Hash(sha256): 3b038e54f690fb3046eccaadb63a8253c494458a9ca8740f2fb86ec9fa8b166c
Signature Hash: f7fba743d5c0494373030d5e5e9b0fd9eb74a5e8e076da39bf9f74ff524b897f
---------------- End Nesting Level 1 ----------------
No CRLs
CertUtil: -dump command completed successfully.
As per this Microsoft KB article, the 1.3.6.1.4.1.311.10.1 object id (OID) identifies a CTL which is a predefined list of items signed by a trusted entity in PKCS7 format. In this instance, boot.stl is a list of trusted root certificates. bootmgfw.efi looks at this file when it is invoked.
So how can you boot your UEFI-based system if you do not have Windows 10 install or recovery media available to you? The answer is quite simple provided you can get to a UEFI shell prompt. From the UEFI shell, you can directly invoke \efi\microsoft\boot\bootmgfw.efi and, provided your firmware NVRAM variables are undamaged, the BCD store is not actually seriously damaged, the NTFS partition is not damaged, Windows 10 should boot as normal.
Note this workaround does not fix any underlying problem; it is simply a useful workaround. You will still have to fix up the BCD store. Once you have Windows 10 booted, you can restore the BCD backup that you made from the command line using bcdedit, or if you used a GUI tool like EasyBCD, recover a good BCD using the EasyBCD Restore Backup option.
I hope this detailed explanation of how Windows 10 boots on a UEFI-platform will help you keep your sanity the next time you boot and see a missing or corrupt BCD message.
Remember to always configure your platform so that you can boot into a UEFI shell using the UEFI firmware-based boot manager and make a backup of your BCD store.
Feel free to ask questions.

Thank you for the one of the most informative explanations of the windows boot process I’ve seen. This was very helpful to me.
a typo in this line:
Note the extra (and critical for repairing the BCD store) information displayed when the /wnum all switch is added:
should be “/enum all”
Thanks for reporting the typo
Howdy I am so grateful I found your website, I
really found you by mistake, while I was browsing on Bing for
something else, Nonetheless I am here now and would just like
to say kudos for a tremendous post and a all round exciting
blog (I also love the theme/design), I don’t have time to go through it all at the minute
but I have bookmarked it and also added in your RSS feeds, so
when I have time I will be back to read much more,
Please do keep up the superb work.
Hello, The explanation is really good and helpful.
I do have a question. I dual-booted win10 and Ubuntu. When I select “Windows” from UEFI boot manager, Win-10 boot normally with OEM logo. But When I select “Ubuntu” from UEFI boot manager and then chainload Win10 from Ubuntu’s grub.cfg file, then though Win-10 boots normally but with Microsoft logo instead of OEM logo. Why is such scenario ? How do I inform Win-10 (from ubuntu) to boot with OEM logo ?
Frankly, I have no real idea. I do not use GRUB2 on any Linux distribution I use; I boot Linux using EFI STUB.
I can only suspect that you are chain loading a different Microsoft OS loader when you boot Windows via GRUB2 than when you boot into Windows 10 from the firmware boot menu.
Hello, very informative indeed.
I’m trying to change the default boot drive to USB HDD and was wondering if you can explain why running “bcdedit /default {def0c63e-218c-11e6-845f-68f7286346fb}” would not make the computer boot from the connected USB HDD after the next restart. Or if you know any other method to programmatically change the default boot drive to USB HDD. Using the advanced startup settings in Windows 10 I can select USB HDD, reboot and it will keep using the USB HDD after each reboot. But setting the GUID {def0c63e-218c-11e6-845f-68f7286346fb} as default with bcdedit doesn’t seem to make any difference.
Thanks,
Dirk
Firmware Application (101fffff) ——————————-
identifier {def0c63e-218c-11e6-845f-68f7286346fb}
description USB HDD